What is OAuth 2.0?
OAuth 2.0 is an industry-standard protocol used to authenticate your apps.
What is OAuth 2.0?
Open Authorization (OAuth) is an authorization protocol that allows one service (application) to be granted permission to access user resources on another service. This protocol eliminates the need to trust the application with credentials and also allows you to issue a limited set of rights, and not all at once.
For more information about OAuth 2.0, refer to RFC 6749 standard.
Workflow
The OAuth 2.0 workflow typically involves the following steps:
- The user requests authorization from the resource owner (in this case client app server).
- If the owner gives authorization, the client passes the authorization grant to the authorization server.
- If the grant is valid, the authorization server returns an access token, possibly alongside a refresh and/or ID token.
- The client now uses that access token to access the resource server.
Token Types
A token is an access key to something, for example, a protected resource (access token) or a new token (refresh Token).
OAuth 2.0 supports various token types, including access tokens, refresh tokens, and bearer tokens. Access tokens provide temporary access to resources, while refresh tokens enable the client to obtain new access tokens without user interaction.
Authorization Code Grant flow
This flow is recommended for most cases. The OAuth 2.0 Authorization Code Grant type (auth code) allows an application to securely access protected resources such as web APIs. The auth code flow requires a user agent that supports redirection from the SchoolDay authorization server back to your application.
During auth code flow:
- The application receives an authorization code after successful user authentication.
- The application exchanges the code for access tokens in exchange for the request.
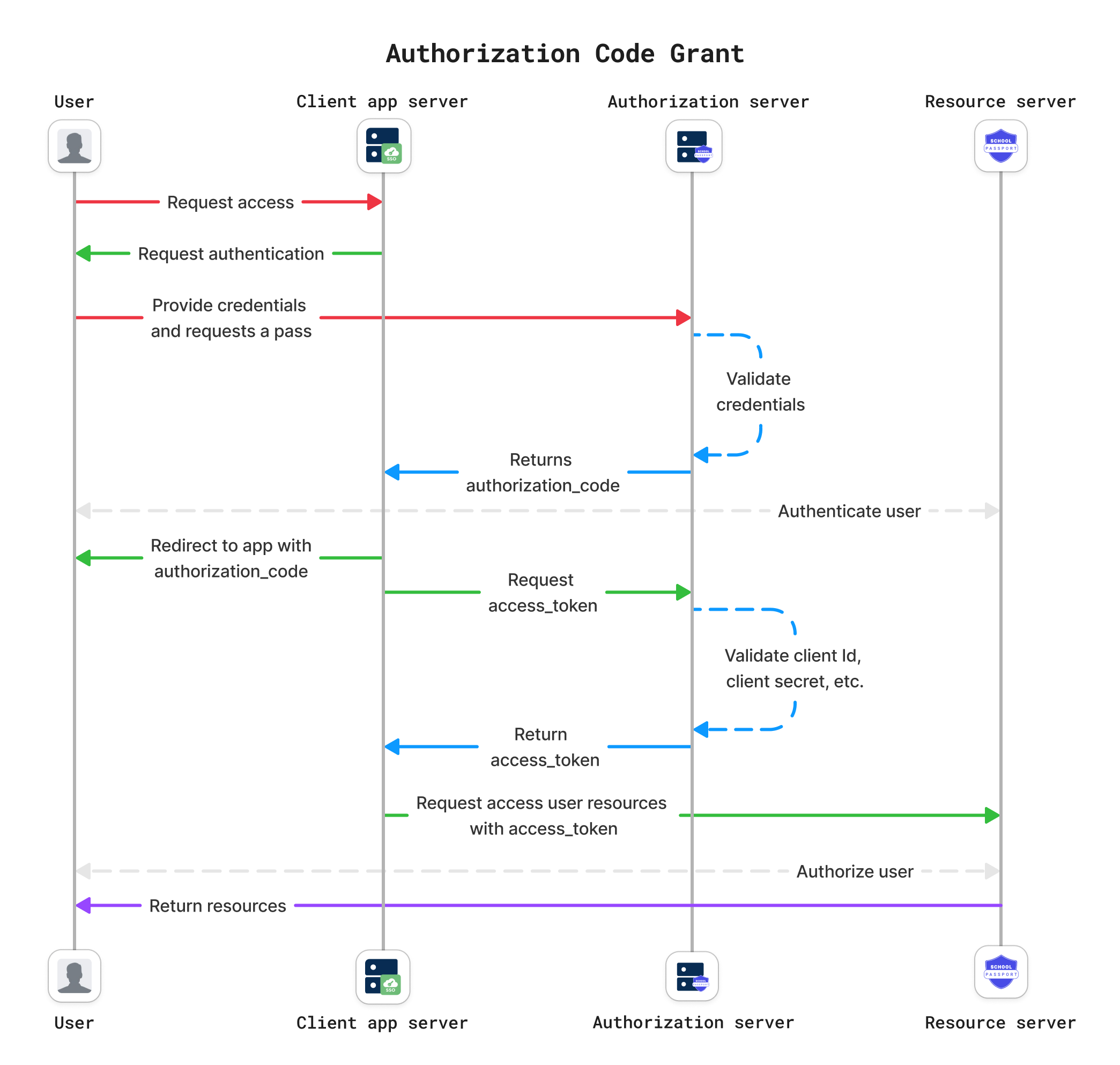
Authorization Code Grant flow
Implicit Grant flow
The OAuth 2.0 Implicit Grant flow allows an application to obtain access tokens directly, without an authorization code exchange step. This flow is not suitable when storing sensitive information on the client side, such as Client Secret. Unlike the Authorization Code Grant, the Implicit Grant delivers the access_token immediately in the redirection URI.
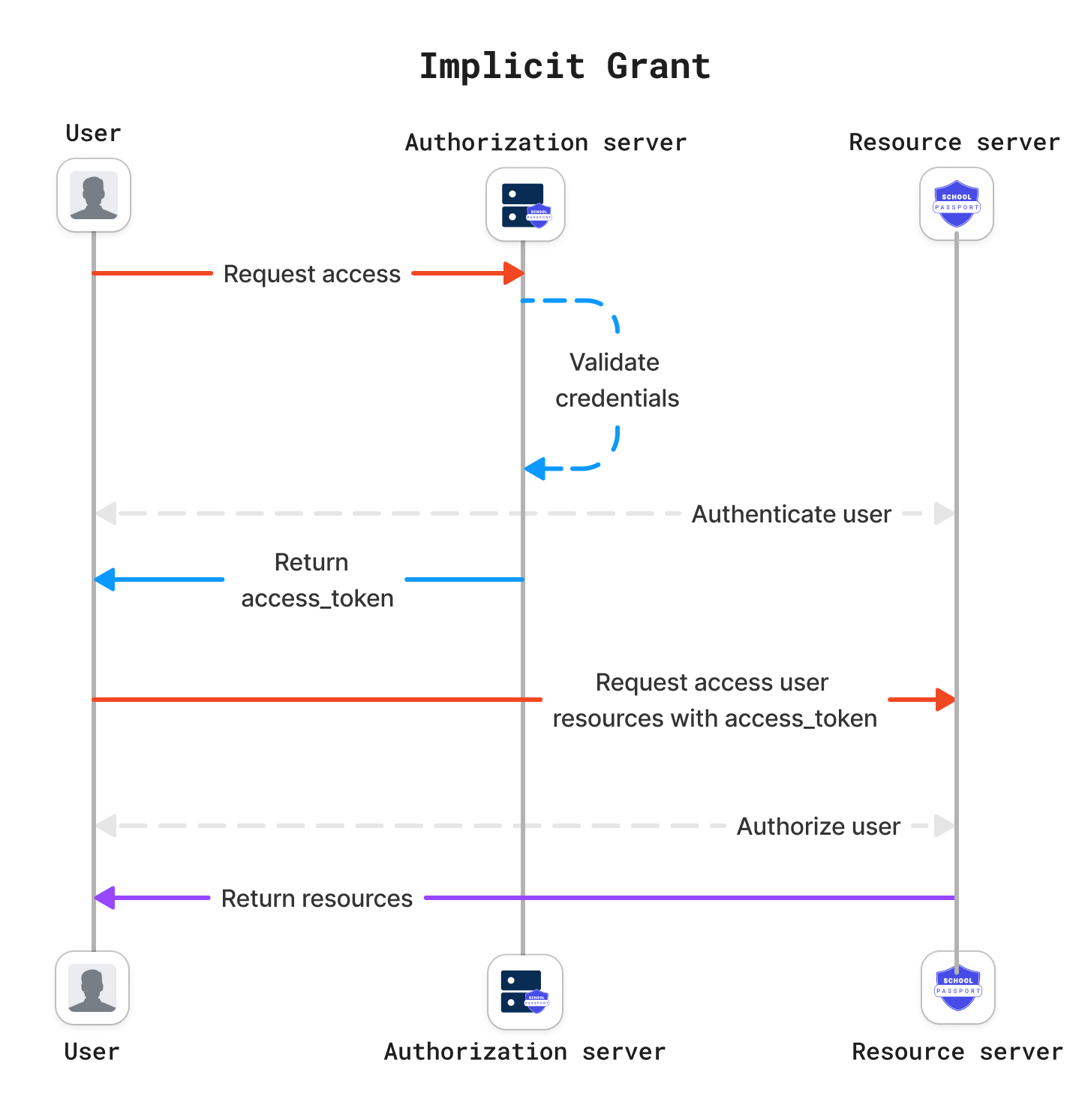
Implicit Grant flow
Resource Owner Password Credentials Grant flow
The OAuth 2.0 Resource Owner Password Credentials (ROPC) Grant flow allows an application to obtain an access token by using the resource owner's username and password directly.
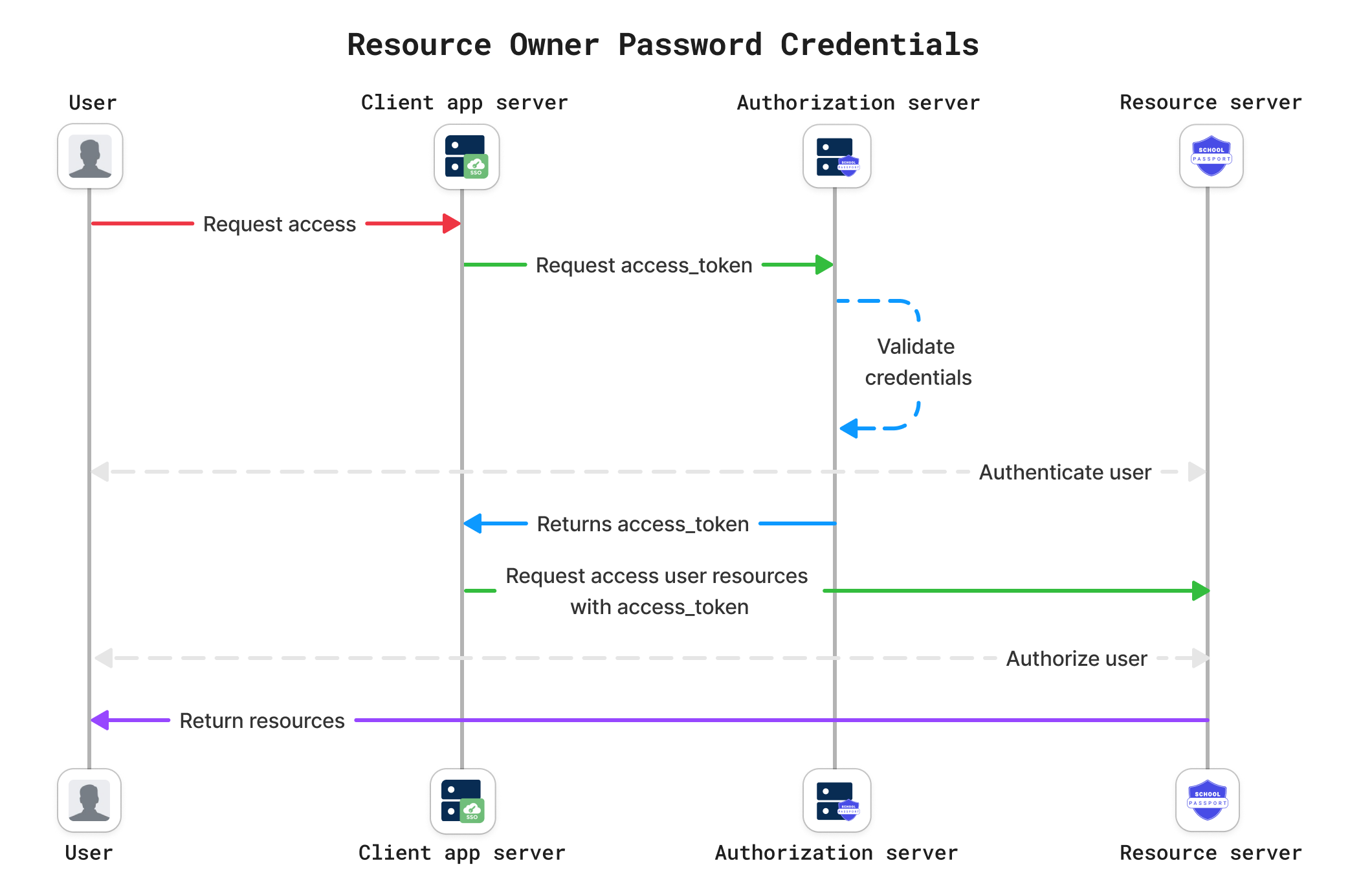
ROPC flow
Updated 10 months ago